Discover why regular website security audits and vulnerability assessments are crucial for safeguarding your online presence and protecting against cyber threats with Techtenstein’s comprehensive guide
Introduce the concept of website security audits and vulnerability assessments as essential components of proactive cybersecurity measures. Emphasize their role in identifying and mitigating potential security risks to ensure the integrity and confidentiality of website data.
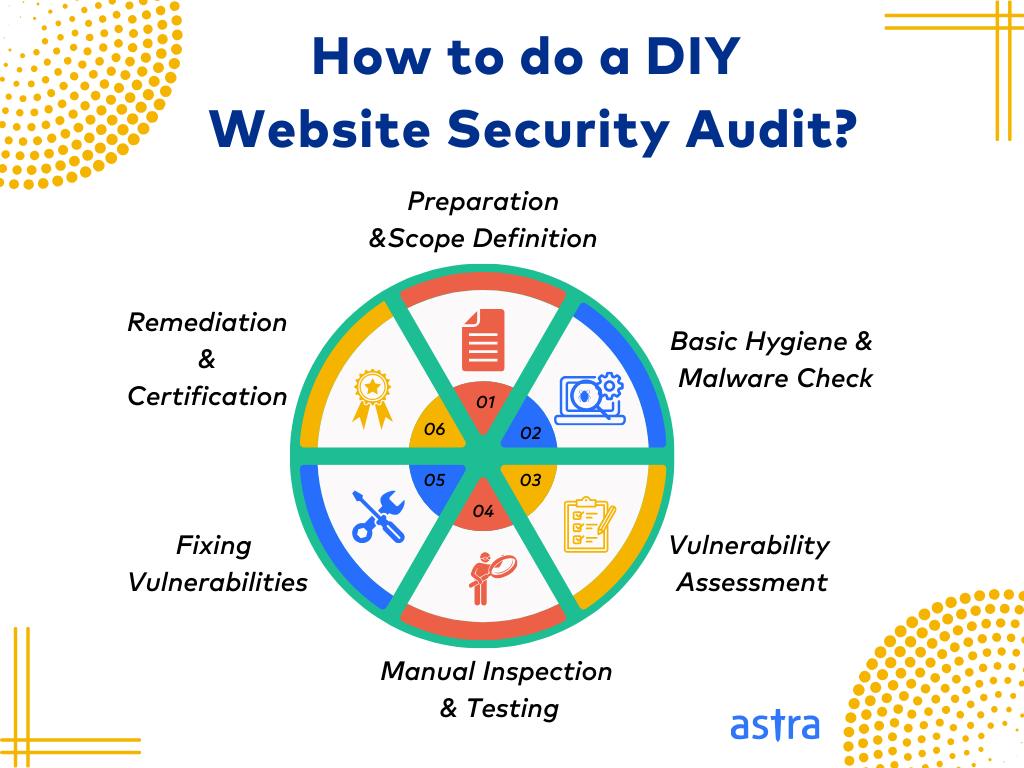
1. Understanding Website Security Audits
- What is a Website Security Audit?
- Define website security audits as systematic evaluations of website infrastructure, code, and configurations to identify security vulnerabilities and weaknesses.
- Objectives of Security Audits
- Discuss the primary goals of security audits, including identifying vulnerabilities, assessing compliance with security standards, and enhancing overall security posture.
2. Importance of Regular Audits
- Proactive Risk Management
- Highlight the importance of conducting regular security audits to proactively identify and address security vulnerabilities before they can be exploited by malicious actors.
- Compliance Requirements
- Discuss how regular audits help ensure compliance with industry regulations and standards, such as GDPR, PCI DSS, and HIPAA, which mandate regular security assessments.
3. Types of Vulnerabilities Assessed
- Common Web Application Vulnerabilities
- Explore common vulnerabilities such as SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms, explaining their potential impact on website security.
- Server and Network Vulnerabilities
- Discuss vulnerabilities related to server misconfigurations, outdated software, and insecure network protocols, highlighting the importance of addressing these issues to prevent exploitation.
4. Vulnerability Assessment Tools and Techniques
- Automated Scanning Tools
- Introduce popular vulnerability assessment tools like Nessus, OpenVAS, and Qualys, which automate the process of scanning websites for known security vulnerabilities.
- Manual Testing and Penetration Testing
- Discuss the benefits of supplementing automated scans with manual testing and penetration testing conducted by cybersecurity professionals to uncover complex vulnerabilities.
5. Best Practices for Conducting Audits
- Establishing Audit Frequency
- Recommend establishing a regular schedule for security audits based on factors such as website complexity, industry regulations, and the frequency of software updates.
- Documentation and Reporting
- Stress the importance of documenting audit findings, prioritizing vulnerabilities based on severity, and preparing comprehensive reports for stakeholders.
6. Addressing Audit Findings
- Patch Management
- Emphasize the importance of promptly addressing identified vulnerabilities through patch management processes, including installing software updates and security patches.
- Implementing Security Controls
- Discuss the implementation of additional security controls and measures to mitigate identified vulnerabilities and strengthen overall website security.
7. Continuous Improvement and Monitoring
- Ongoing Security Awareness
- Advocate for promoting a culture of security awareness among website administrators and users, emphasizing the importance of staying vigilant against emerging threats.
- Continuous Monitoring
- Highlight the need for continuous monitoring of website security status, including real-time threat detection, incident response preparedness, and regular reassessment of security controls.
8.Mitigation Strategies and Remediation
- Prioritizing Vulnerabilities
- Explain the importance of prioritizing identified vulnerabilities based on their severity, potential impact, and exploitability, to focus resources on addressing the most critical risks first.
- Implementing Security Patches
- Advocate for promptly applying security patches and updates to address known vulnerabilities and mitigate the risk of exploitation by malicious actors.
9.Compliance Requirements and Regulatory Standards
- Industry Regulations
- Discuss how compliance requirements, such as GDPR, HIPAA, PCI DSS, and others, mandate regular website security audits and vulnerability assessments to protect sensitive data and ensure regulatory compliance.
- Legal Obligations
- Highlight the legal obligations of website owners and operators to maintain adequate security measures and protect user information from unauthorized access or disclosure.
In conclusion, regular website security audits and vulnerability assessments are essential for proactively identifying and mitigating security risks, ensuring the integrity and confidentiality of website data. Summarize the key points discussed in the article and stress the importance of integrating security audits into your organization’s cybersecurity strategy to protect against evolving cyber threats effectively



