Safeguard your website from DDoS attacks with expert strategies and solutions outlined in Techtenstein’s comprehensive guide, ensuring uninterrupted online presence and user experience.
Highlight the growing threat of Distributed Denial of Service (DDoS) attacks targeting websites and their detrimental impact on availability and performance. Emphasize the importance of proactive measures to mitigate DDoS risks.
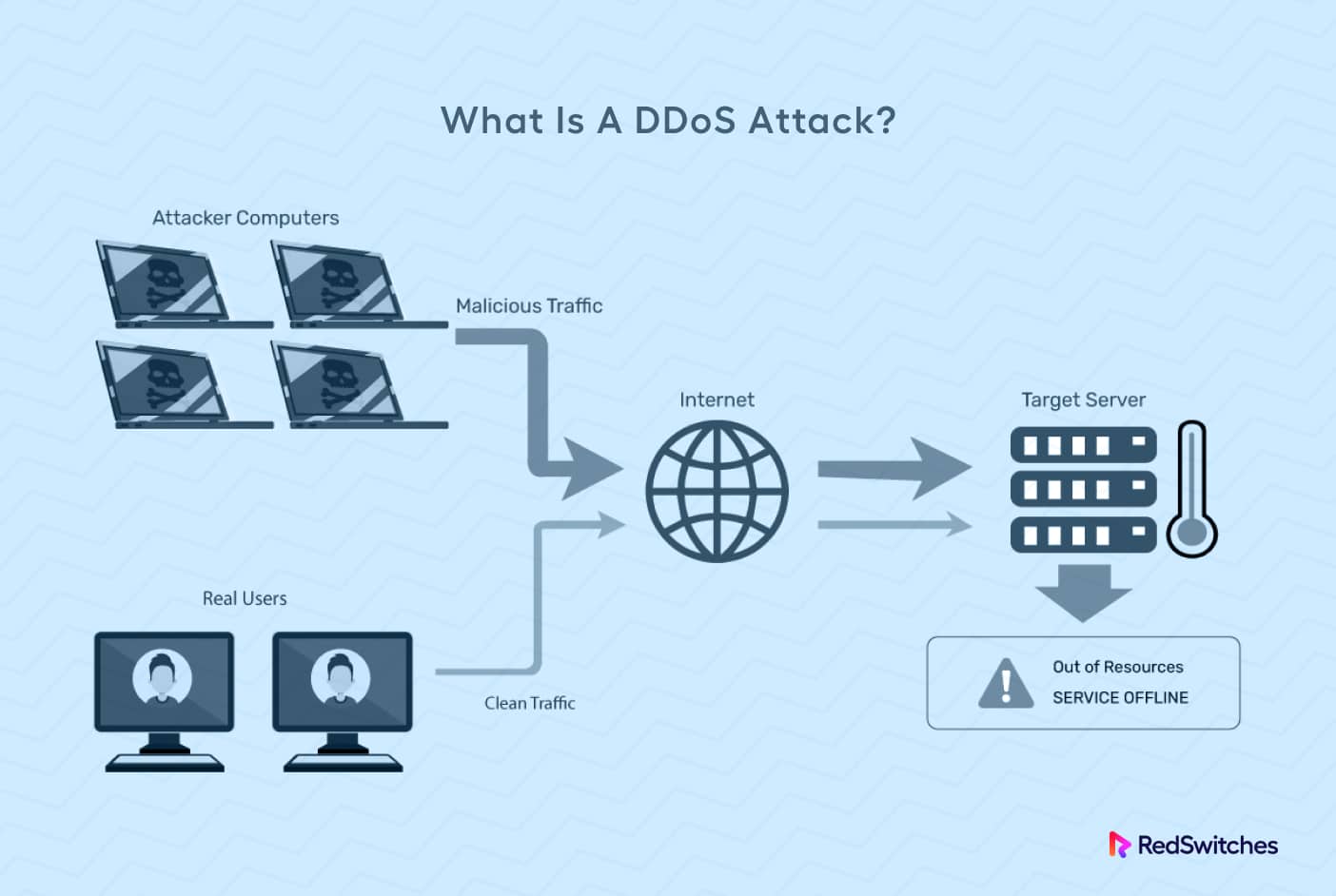
1. Understanding DDoS Attacks
- What is a DDoS Attack?
- Define DDoS attacks as malicious attempts to disrupt the normal functioning of a website or online service by overwhelming it with a flood of traffic from multiple sources.
- Types of DDoS Attacks
- Explore various DDoS attack methods, including volumetric attacks, protocol attacks, and application-layer attacks, explaining their characteristics and objectives.
2. Impact of DDoS Attacks on Websites
- Availability and Downtime
- Discuss how DDoS attacks can render websites inaccessible to legitimate users, resulting in downtime and loss of revenue for businesses.
- Reputation Damage
- Highlight the potential damage to brand reputation and customer trust caused by frequent or prolonged outages due to DDoS attacks.
3. DDoS Protection Strategies
- Traffic Scrubbing Services
- Explain the role of traffic scrubbing services in mitigating DDoS attacks by filtering malicious traffic and allowing legitimate traffic to reach the website.
- Content Delivery Networks (CDNs)
- Discuss how CDNs can help mitigate DDoS attacks by distributing website content across multiple servers and absorbing attack traffic closer to the source.
4. Implementing Rate Limiting and Traffic Filtering
- Rate Limiting
- Describe how rate limiting techniques can be used to restrict the number of requests from individual IP addresses or user agents, preventing excessive traffic from overwhelming the website.
- Traffic Filtering
- Explore the use of traffic filtering solutions, such as intrusion prevention systems (IPS) and web application firewalls (WAFs), to identify and block malicious traffic before it reaches the web server.
5. Leveraging DDoS Mitigation Appliances
- Purpose-built Appliances
- Introduce purpose-built DDoS mitigation appliances designed to detect and mitigate DDoS attacks in real-time, providing an additional layer of defense against volumetric attacks.
- On-premises vs. Cloud-based Solutions
- Compare the benefits and considerations of on-premises DDoS mitigation appliances versus cloud-based DDoS protection services, helping businesses choose the right solution for their needs.
6. Building Resilience with Redundant Infrastructure
- Redundant Network Architecture
- Explain the importance of building redundancy into the network infrastructure to withstand DDoS attacks and maintain service availability during peak traffic periods.
- Failover Mechanisms
- Discuss failover mechanisms and load balancing strategies to automatically reroute traffic away from overloaded servers or network segments in the event of a DDoS attack.
7. Monitoring and Incident Response
- Real-time Monitoring
- Emphasize the importance of real-time monitoring for early detection of DDoS attacks, enabling prompt response and mitigation efforts.
- Incident Response Plan
- Recommend the development of a comprehensive incident response plan outlining roles, responsibilities, and procedures for responding to DDoS attacks swiftly and effectively.
8.Continuous Monitoring and Threat Intelligence
- Real-Time Traffic Analysis
- Highlight the importance of continuous monitoring of network traffic and server performance to detect anomalies and potential DDoS attacks.
- Threat Intelligence Integration
- Discuss the benefits of integrating threat intelligence feeds into DDoS detection systems to stay informed about emerging threats and adapt mitigation strategies accordingly.
9.Incident Response and Recovery
- DDoS Incident Response Plan
- Emphasize the need for developing a comprehensive DDoS incident response plan, including predefined roles and responsibilities, escalation procedures, and communication protocols.
- Backup and Redundancy
- Advocate for maintaining regular backups of website data and implementing redundancy measures to quickly restore services in the event of a DDoS attack.
10.Strengthening Infrastructure Resilience
- Scalable Architecture
- Discuss the importance of designing scalable infrastructure capable of handling sudden surges in traffic without succumbing to DDoS attacks.
- Load Balancing
- Explain how load balancers distribute incoming traffic across multiple servers, preventing overload and ensuring continuous availability of web services.
11.DDoS Mitigation Techniques
- Content Delivery Network (CDN)
- Advocate for leveraging CDNs to distribute website content across multiple servers, improving performance and resilience against DDoS attacks by dispersing traffic.
- Cloud-Based DDoS Protection Services
- Explore the benefits of utilizing cloud-based DDoS protection services offered by specialized providers, enabling rapid detection and mitigation of DDoS threats.
12.Strategies for DDoS Attack Prevention
- Implementing Network Security Measures
- Explain the importance of deploying firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to filter and block malicious traffic.
- Rate Limiting and Traffic Shaping
- Discuss the use of rate limiting and traffic shaping techniques to regulate incoming traffic and mitigate the impact of DDoS attacks.
In conclusion, protecting your website from DDoS attacks requires a multi-layered approach combining proactive measures, advanced technologies, and vigilant monitoring. Summarize key strategies outlined in the article and encourage readers to prioritize DDoS defense to safeguard their online presence and reputation.



