Discover how TechTenStein’s proven web security strategies can protect and enhance your business in Tirupati.
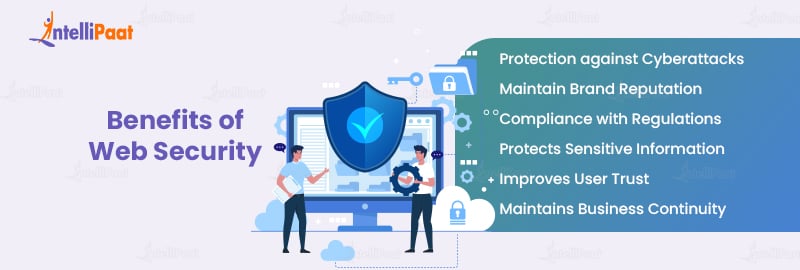
The Rising Importance of Web Security for Entrepreneurs
In the digital age, web security is no longer a luxury but a necessity. For entrepreneurs in Tirupati, ensuring the security of their online presence is critical for business success. Cyber threats are constantly evolving, and a robust web security strategy is essential to protect sensitive data, maintain customer trust, and ensure business continuity.
Why Choose TechTenStein?
TechTenStein is a leading provider of comprehensive web security solutions tailored specifically for entrepreneurs. With a focus on innovation and excellence, TechTenStein has established itself as a trusted partner in safeguarding businesses from cyber threats.
Understanding Web Security
1. The Nature of Cyber Threats
To understand the importance of web security, it is crucial to recognize the various types of cyber threats that businesses face.
- Malware: Malicious software designed to damage or disrupt systems.
- Phishing: Deceptive attempts to steal sensitive information.
- Ransomware: Malware that locks data until a ransom is paid.
- DDoS Attacks: Overwhelming a website with traffic to make it inaccessible.
- SQL Injection: Exploiting vulnerabilities in web applications to manipulate databases.
- Cross-Site Scripting (XSS): Injecting malicious scripts into webpages viewed by users.
- Brute Force Attacks: Attempting to gain access through trial and error of passwords.
2. The Impact of Cyber Attacks on Businesses
Cyber attacks can have devastating effects on businesses, including:
- Financial Loss: Direct financial impact from theft or ransom payments.
- Reputational Damage: Loss of customer trust and potential negative publicity.
- Operational Disruptions: Interruptions in business operations and productivity.
- Legal Consequences: Non-compliance with data protection regulations can lead to fines and legal action.
The Need for Comprehensive Web Security
1. Protecting Sensitive Data
Businesses handle a vast amount of sensitive data, from customer information to financial records. Protecting this data is critical to maintaining trust and ensuring compliance with regulations.
- Data Encryption: Encrypting data at rest and in transit to prevent unauthorized access.
- Secure Storage Solutions: Implementing secure storage to protect sensitive information.
- Access Controls: Restricting access to sensitive data to authorized personnel only.
2. Maintaining Customer Trust
Customer trust is essential for business success. A security breach can severely damage a company’s reputation and erode customer confidence.
- Transparent Security Policies: Clearly communicating security policies to customers.
- Regular Security Audits: Conducting regular audits to identify and address vulnerabilities.
- Prompt Incident Response: Responding quickly and effectively to security incidents.
3. Ensuring Business Continuity
Cyber attacks can disrupt business operations, leading to downtime and loss of productivity. Robust security measures ensure business continuity and minimize operational disruptions.
- Backup Solutions: Implementing reliable backup solutions to restore operations quickly after an attack.
- Disaster Recovery Plans: Developing and testing disaster recovery plans.
- Continuous Monitoring: Monitoring systems continuously to detect and respond to threats in real-time.
4. Complying with Regulations
Compliance with data protection regulations is essential to avoid legal consequences and fines. Regulations such as GDPR and HIPAA mandate stringent security measures to protect sensitive data.
- Regular Compliance Audits: Ensuring compliance with regulations through regular audits.
- Employee Training: Training employees on regulatory requirements and best practices.
- Documentation and Reporting: Maintaining accurate records and reporting security incidents as required by law.
TechTenStein’s Proven Web Security Strategies
1. Comprehensive Security Assessments
TechTenStein begins with a thorough assessment of your current security posture. This involves identifying vulnerabilities and potential threats.
- Risk Assessments: Evaluating potential risks and vulnerabilities unique to your business.
- Penetration Testing: Simulating cyber attacks to identify weaknesses in your defenses.
- Security Audits: Conducting detailed audits to assess the effectiveness of your existing security measures.
2. Customized Security Solutions
Based on the assessment, TechTenStein develops customized security solutions tailored to your business needs.
- Network Security: Implementing firewalls, intrusion detection, and prevention systems to secure your network.
- Endpoint Security: Protecting all devices connected to your network from potential threats.
- Application Security: Ensuring the security of your web applications through regular assessments and secure coding practices.
3. Advanced Threat Detection and Response
TechTenStein employs advanced threat detection and response capabilities to quickly identify and mitigate potential threats.
- Real-Time Monitoring: Continuous monitoring of your digital infrastructure to detect and respond to threats in real-time.
- Threat Intelligence: Leveraging the latest threat intelligence to stay ahead of cyber threats.
- Automated Response: Implementing automated response measures to quickly address threats.
4. Proactive Security Measures
TechTenStein believes in a proactive approach to security, focusing on prevention rather than reaction.
- Regular Updates and Patches: Ensuring all systems are up-to-date with the latest security patches.
- Continuous Improvement: Regularly reviewing and improving security measures.
- Security Awareness Programs: Conducting regular training sessions for employees to promote safe online behavior.
5. 24/7 Support and Monitoring
TechTenStein provides round-the-clock support and monitoring to ensure that your business remains secure at all times.
- Security Operations Center (SOC): Offering 24/7 monitoring and incident response.
- Rapid Incident Response: Quickly addressing and mitigating security incidents.
- Ongoing Support: Providing continuous support and guidance to our clients.
Case Studies: TechTenStein’s Success Stories
Case Study 1: Healthcare Provider Security Enhancement
A healthcare provider in Tirupati faced challenges in protecting patient data and complying with regulatory requirements. TechTenStein conducted a comprehensive security audit and implemented robust data encryption, secure access controls, and continuous monitoring. These measures ensured compliance and protected sensitive patient information.
Case Study 2: E-Commerce Business Protection
An e-commerce business in Tirupati experienced frequent cyberattacks that affected its operations. TechTenStein implemented a multi-layered security strategy, including firewall protection, regular vulnerability assessments, and endpoint security solutions. This approach significantly reduced cyber incidents and increased customer trust.
Case Study 3: Financial Services Firm Security
A financial services firm needed to comply with stringent regulatory requirements and protect client data. TechTenStein provided data encryption, secure access controls, and continuous monitoring services. These measures ensured compliance with regulations and safeguarded the firm’s critical data.
The Future of Web Security
Emerging Threats and Challenges
As technology evolves, so do cyber threats. Businesses must stay informed about emerging threats and challenges to remain protected.
- Artificial Intelligence (AI) and Machine Learning (ML) Attacks: Cybercriminals are leveraging AI and ML to develop more sophisticated attacks.
- Internet of Things (IoT) Security: The proliferation of IoT devices introduces new security challenges.
- Cloud Security: As more businesses move to the cloud, securing cloud environments becomes crucial.
Innovative Security Solutions
TechTenStein is committed to staying at the forefront of web security by developing and implementing innovative solutions.
- AI and ML for Security: Leveraging AI and ML to detect and respond to threats more effectively.
- Zero Trust Architecture: Adopting a zero-trust approach to enhance security.
- Blockchain Technology: Exploring the use of blockchain for secure transactions and data integrity.
The Necessity of Web Security for Tirupati Entrepreneurs
In an increasingly digital world, web security is essential for protecting your business from cyber threats. Tirupati entrepreneurs must prioritize security to safeguard their data, maintain customer trust, and ensure long-term success.
TechTenStein: Your Trusted Partner in Web Security
TechTenStein offers comprehensive web security services tailored to the unique needs of Tirupati businesses. Our expertise, cutting-edge technology, and customer-centric approach make us the ideal partner for securing your business.
Act Now for a Secure Future
Don’t wait for a cyber incident to impact your business. Contact TechTenStein today to discover how our web security services can protect your business and provide peace of mind.
Appendix: Additional Resources
1. Glossary of Web Security Terms
- Malware: Malicious software designed to damage or disrupt systems.
- Phishing: Deceptive attempts to steal sensitive information.
- Ransomware: Malware that locks data until a ransom is paid.
- DDoS Attacks: Overwhelming a website with traffic to make it inaccessible.
- SQL Injection: Exploiting vulnerabilities in web applications to manipulate databases.
- Cross-Site Scripting (XSS): Injecting malicious scripts into webpages viewed by users.
- Brute Force Attacks: Attempting to gain access through trial and error of passwords.
2. Web Security Best Practices
- Use Strong Passwords: Implement strong password policies to protect accounts.
- Enable Two-Factor Authentication: Add an extra layer of security by requiring a second form of authentication.
- Regularly Update Software: Keep all software up-to-date with the latest security patches.
- Conduct Regular Security Audits: Regularly review and assess your security measures.
- Educate Employees: Train employees on security best practices and how to recognize potential threats.



